$ORACLE_HOME/bin/sqlplus –s /nologin<
connect system/manager as sysdba;
alter system set db_cache_size=10m;
alter system flush buffer_cache;
exit
Oracle RAC installation Steps | Installing Oracle Database 10g Real Application Cluster (RAC)
Steps/Procedures for Oracle RAC installation:
Pre-Intsllation Steps:
1.User Creation.
OSDBA group(dba)
OSOPER group(oper)
Oracle Inventory group(oinstall)
Oracle software owner user(oracle)
2.Configure SSH
3.Configure User Environment
4.Check Hardware Requirements
5.Check Network Requirements
6.Check Software Requirement
7.Configure Symbolic Links
8.Configure Kernal Parameters
9.Checking the Required Base Directories
10. Storage Creation for Clusterware files.
Installation Steps:
1.Verify the Prerequisites of the Clusterware with the CVU using the command.
/mountpoint/crs/Disk1/cluvfy/runcluvfy.sh stage -pre crsinst -n node_list
2.Install Clusterware
3.Verify the Prerequisites of the RAC Database with the CVU using the command.
/mountpoint/crs/Disk1/cluvfy/runcluvfy.sh stage -pre dbinst -n node_list [-r
{10gR1
10gR2}] [-osdba osdba_group][-verbose]
4.Install Oracle RAC
5.Create Database.
Pre-Intsllation Steps:
1.User Creation.
OSDBA group(dba)
OSOPER group(oper)
Oracle Inventory group(oinstall)
Oracle software owner user(oracle)
2.Configure SSH
3.Configure User Environment
4.Check Hardware Requirements
5.Check Network Requirements
6.Check Software Requirement
7.Configure Symbolic Links
8.Configure Kernal Parameters
9.Checking the Required Base Directories
10. Storage Creation for Clusterware files.
Installation Steps:
1.Verify the Prerequisites of the Clusterware with the CVU using the command.
/mountpoint/crs/Disk1/cluvfy/runcluvfy.sh stage -pre crsinst -n node_list
2.Install Clusterware
3.Verify the Prerequisites of the RAC Database with the CVU using the command.
/mountpoint/crs/Disk1/cluvfy/runcluvfy.sh stage -pre dbinst -n node_list [-r
{10gR1
10gR2}] [-osdba osdba_group][-verbose]
4.Install Oracle RAC
5.Create Database.
Setting the Java classpath in Windows through command prompt
Q: How to set path for java in windows through command prompt. I don't want to set path permanently from my computer icon with advanced tab with environment variables . what is command to set path for java
CLASSPATH
In JDK the CLASSPATH contains directories (or JAR files), from where your java compiler/runtime will look for .class files (and some others). For example, "java Hello.class" will not work unless you set the directory (or JAR file) Hello.class is in, into your CLASSPATH.
i.e.classpath C:\Java\jdk1.6.0_03\lib
For setting CLASSPATH using command prompt
Java class path can be set using either the -classpath option when calling an SDK tool (the preferred method) or by setting the CLASSPATH environment variable. The -classpath option is preferred because you can set it individually for each application without affecting other applications and without other applications modifying its value.
(ii)on command prompt
C:\>set classpath=%classpath;C:\Java\jdk1.6.0_03\lib%
CLASSPATH
In JDK the CLASSPATH contains directories (or JAR files), from where your java compiler/runtime will look for .class files (and some others). For example, "java Hello.class" will not work unless you set the directory (or JAR file) Hello.class is in, into your CLASSPATH.
i.e.classpath C:\Java\jdk1.6.0_03\lib
For setting CLASSPATH using command prompt
Java class path can be set using either the -classpath option when calling an SDK tool (the preferred method) or by setting the CLASSPATH environment variable. The -classpath option is preferred because you can set it individually for each application without affecting other applications and without other applications modifying its value.
(ii)on command prompt
C:\>set classpath=%classpath;C:\Java\jdk1.6.0_03\lib%
JSP Life Cycle Explanation

JSP’s life cycle can be grouped into following phases.
1. JSP Page Translation:
A java servlet file is generated from the JSP source file. This is the first step in its tedious multiple phase life cycle. In the translation phase, the container validates the syntactic correctness of the JSP pages and tag files. The container interprets the standard directives and actions, and the custom actions referencing tag libraries used in the page.2. JSP Page Compilation:
The generated java servlet file is compiled into a java servlet class.Note: The translation of a JSP source page into its implementation class can happen at any time between initial deployment of the JSP page into the JSP container and the receipt and processing of a client request for the target JSP page.
3. Class Loading:
The java servlet class that was compiled from the JSP source is loaded into the container.4. Execution phase:
In the execution phase the container manages one or more instances of this class in response to requests and other events.The interface JspPage contains jspInit() and jspDestroy(). The JSP specification has provided a special interface HttpJspPage for JSP pages serving HTTP requests and this interface contains _jspService().
5. Initialization:
jspInit() method is called immediately after the instance was created. It is called only once during JSP life cycle.6. _jspService() execution:
This method is called for every request of this JSP during its life cycle. This is where it serves the purpose of creation. Oops! it has to pass through all the above steps to reach this phase. It passes the request and the response objects. _jspService() cannot be overridden.7. jspDestroy() execution:
This method is called when this JSP is destroyed. With this call the servlet serves its purpose and submits itself to heaven (garbage collection). This is the end of jsp life cycle.jspInit(), _jspService() and jspDestroy() are called the life cycle methods of the JSP.
What is the difference in using request.getRequestDispatcher() and context.getRequestDispatcher()?
In request.getRequestDispatcher(path) in order to create it we need to give the relative path of the resource. But in resourcecontext.getRequestDispatcher(path) in order to create it we need to give the absolute path of the resource.
Life-cycle mehtods in JSP
THe generated servlet class for a JSP page implements the HttpJspPage interface of the javax.servlet.jsp package. Hte HttpJspPage interface extends the JspPage interface which inturn extends the Servlet interface of the javax.servlet package. the generated servlet class thus implements all the methods of the these three interfaces. The JspPage interface declares only two mehtods - jspInit() and jspDestroy() that must be implemented by all JSP pages regardless of the client-server protocol. However the JSP specification has provided the HttpJspPage interfaec specifically for the JSp pages serving HTTP requests. This interface declares one method _jspService().
The jspInit()- The container calls the jspInit() to initialize te servlet instance.It is called before any other method, and is called only once for a servlet instance.
The _jspservice()- The container calls the _jspservice() for each request, passing it the request and the response objects.
The jspDestroy()- The container calls this when it decides take the instance out of service. It is the last method called n the servlet instance.
The jspInit()- The container calls the jspInit() to initialize te servlet instance.It is called before any other method, and is called only once for a servlet instance.
The _jspservice()- The container calls the _jspservice() for each request, passing it the request and the response objects.
The jspDestroy()- The container calls this when it decides take the instance out of service. It is the last method called n the servlet instance.
scope values for the <jsp:useBean>?
The different scope values for are
1. page
2. request
3.session
4.application
2. request
3.session
4.application
Difference between JSP and Servlets
interview questions for JSP and Servlets only. Since JSP and Servlets are almost identical technology, there is only one section for both JSP and Servlet interview questions. If you need interview questions for any other java related technologies , please check the relevant sections.
Difference between JSP and Servlets
JSP is used mainly for presentation only. A JSP can only be HttpServlet that means the only supported protocol in JSP is HTTP. But a servlet can support any protocol like HTTP, FTP, SMTP etc.
Difference between JSP and Servlets
JSP is used mainly for presentation only. A JSP can only be HttpServlet that means the only supported protocol in JSP is HTTP. But a servlet can support any protocol like HTTP, FTP, SMTP etc.
Mainframe Interview Questions,DB2 Administration Interview Questions, DB2 UDB Admin Interview Questions,DB2 Admin Interview
If you are given with a query, how you tune it?
Does runstats do a sort?
Explain the steps of Server Installation?
Explain the steps of Disaster Recovery?
What is Increamental /Delta Back up ?
What are the db cfg parms which affect the back up strategy?
Have you worked in partitioned DB ?
How to check no of active conncetions to the DB >> db2 list active databases
The Application team contacts saying DB response is very low what would you do ?
What is a Global Declared Temporary table ? How to use it ?
What is runstats ? how it improves performance ?
What is HADR ? How to load data to a HADR Server ?
SMS table space is full, filesystem is also full , Cannot add SAN what would you do ?
Have you worked in Partitioned DB ?
What are the tables spaces that get created when a DB is initially created,?
What is the use of SYSCAT SPACE ?
What is the use of buffer pools ?
What is buffer pool hit ratio ?
How would you see the buffer pool usage?
How do you find out deadlock transaction ?
What is Reorg check?
Whats are the different Back up types ?
Do you write shell scripts ?
Other than space utilization what is the difference between DMS and SMS ?
How do you find containers that are in error with out looking into diaglog ?
What DB parameter must be set to allow to take incremental back up ?
Does runstats do a sort?
Explain the steps of Server Installation?
Explain the steps of Disaster Recovery?
What is Increamental /Delta Back up ?
What are the db cfg parms which affect the back up strategy?
Have you worked in partitioned DB ?
How to check no of active conncetions to the DB >> db2 list active databases
The Application team contacts saying DB response is very low what would you do ?
What is a Global Declared Temporary table ? How to use it ?
What is runstats ? how it improves performance ?
What is HADR ? How to load data to a HADR Server ?
SMS table space is full, filesystem is also full , Cannot add SAN what would you do ?
Have you worked in Partitioned DB ?
What are the tables spaces that get created when a DB is initially created,?
What is the use of SYSCAT SPACE ?
What is the use of buffer pools ?
What is buffer pool hit ratio ?
How would you see the buffer pool usage?
How do you find out deadlock transaction ?
What is Reorg check?
Whats are the different Back up types ?
Do you write shell scripts ?
Other than space utilization what is the difference between DMS and SMS ?
How do you find containers that are in error with out looking into diaglog ?
What DB parameter must be set to allow to take incremental back up ?
CICS Interview Questions asked in various MNCs like TCS,Wipro,Infosys,HP Dell and IBM-Part 3
What is ASRAABEND in CICS ?
What is a Logical Unit of Work (LUW) ?
What does Pseudo Conversational mean?
What are the various types of accesses that can be allowed by the SERVREQ option of the
DFHFCT
What are the differences between Temporary Storage Queue (TSQ) and Transient Data Quene (TDQ)?
What are the attribute values of Skipper and Stopper fields?
The process of writting its own type of journal records by the application program
Reading a record from a TSQ will logically delete the record from the Queue (True or False).
Name some command used for CICS file browsing.
In which CICS table would you specify the length of the TASK WORK AREA (TWA)?
How would you resolve an ASRA abend?
How is the storage determined in the symbolic map, if you have multiple maps ?
How do you make your BMS maps case sensitive
How do you define Task Work Area?
How and where is the TWA size set?
Explain re-entrancy as applies to CICS.
Can you define multiple maps in a BMS mapset
A CICS program ABENDS with an ASRA ABEND code, What is its meaning ?
What is a Logical Unit of Work (LUW) ?
What does Pseudo Conversational mean?
What are the various types of accesses that can be allowed by the SERVREQ option of the
DFHFCT
What are the differences between Temporary Storage Queue (TSQ) and Transient Data Quene (TDQ)?
What are the attribute values of Skipper and Stopper fields?
The process of writting its own type of journal records by the application program
Reading a record from a TSQ will logically delete the record from the Queue (True or False).
Name some command used for CICS file browsing.
In which CICS table would you specify the length of the TASK WORK AREA (TWA)?
How would you resolve an ASRA abend?
How is the storage determined in the symbolic map, if you have multiple maps ?
How do you make your BMS maps case sensitive
How do you define Task Work Area?
How and where is the TWA size set?
Explain re-entrancy as applies to CICS.
Can you define multiple maps in a BMS mapset
A CICS program ABENDS with an ASRA ABEND code, What is its meaning ?
CICS Interview Questions asked in various MNCs like TCS,Wipro,Infosys,HP Dell and IBM-Part 2
Name and explain some common CICS abend codes?
In the CICS command level all the re-entrancy issues are handled by the System (True or
False).?
How would you release control of the record in a READ for UPDATE?
How is the stopper byte different from an auto byte?
How do you invoke other programs? What are the pros and cons of each method?
How do you control cursor positioning?
For multithreading an apllication program need not be re-entrant(True or False).
Explain how to handle exceptional conditions in CICS.
CICS Command level is?
Can you access QSAM (seq) files from CICS?
Why must all CICS programs have a Linkage Section?
Which is the program which determines whether a transaction should be restarted?
Which CICS system program is responsible for handling automatic task initialization?
What us the primary function of the Sign-on Table ?
What is the size of commarea ?
What is the meaning of the SYNCPOINT command?
What is the function of the CICS translator ?
What is the difference between the enter key, the PF keys and the PA keys
What is the difference between a RETURN
What is the command used for receiving a map from a terminal?
What is the CICS Command that is used for reading a record from the TDQ?
What is meant by program reentrance?
What is effect on RECEIVE MAP when PF key is pressed? PA key is pressed?
In the CICS command level all the re-entrancy issues are handled by the System (True or
False).?
How would you release control of the record in a READ for UPDATE?
How is the stopper byte different from an auto byte?
How do you invoke other programs? What are the pros and cons of each method?
How do you control cursor positioning?
For multithreading an apllication program need not be re-entrant(True or False).
Explain how to handle exceptional conditions in CICS.
CICS Command level is?
Can you access QSAM (seq) files from CICS?
Why must all CICS programs have a Linkage Section?
Which is the program which determines whether a transaction should be restarted?
Which CICS system program is responsible for handling automatic task initialization?
What us the primary function of the Sign-on Table ?
What is the size of commarea ?
What is the meaning of the SYNCPOINT command?
What is the function of the CICS translator ?
What is the difference between the enter key, the PF keys and the PA keys
What is the difference between a RETURN
What is the command used for receiving a map from a terminal?
What is the CICS Command that is used for reading a record from the TDQ?
What is meant by program reentrance?
What is effect on RECEIVE MAP when PF key is pressed? PA key is pressed?
CICS Interview Questions asked in various MNCs like TCS,Wipro,Infosys,HP Dell and IBM-Part 1
Which is the option of the HANDLE AID command
Which CICS command must be issued by the application program
What table must be update when adding a new transaction and program?
What is the significance of RDO?
What is the meaning of the ENQ and DEQ commands?
What is the function of DFHMDF BMS macro?
What is the difference between START and XCTL ?
What is the difference between a physical BMS mapset and a logical BMS mapset ?
What is the command that is used to delay the processing of a task for a specified time interval
or until a specified time?
What is the CICS command that gives the length of TWA area?
What is meant by a CICS task?
What is difference between call and link ?
What is an MDT ?
What is a logical message in CICS?
What does it mean when EIBCALEN is equal to zeros?
What are the two ways of breaking a CPU bound process to allow other task to gain access to CPU.
What are the differences between DFHCOMMAREA and TSQ?
What are the 3 working storage fields used for every field on the map?
Which CICS command must be issued by the application program
What table must be update when adding a new transaction and program?
What is the significance of RDO?
What is the meaning of the ENQ and DEQ commands?
What is the function of DFHMDF BMS macro?
What is the difference between START and XCTL ?
What is the difference between a physical BMS mapset and a logical BMS mapset ?
What is the command that is used to delay the processing of a task for a specified time interval
or until a specified time?
What is the CICS command that gives the length of TWA area?
What is meant by a CICS task?
What is difference between call and link ?
What is an MDT ?
What is a logical message in CICS?
What does it mean when EIBCALEN is equal to zeros?
What are the two ways of breaking a CPU bound process to allow other task to gain access to CPU.
What are the differences between DFHCOMMAREA and TSQ?
What are the 3 working storage fields used for every field on the map?
IBM CICS Frequently Asked Interview Questions,CICS Interview Questions
IBM CICS Frequently Asked Interview Questions , below are some important CICS Interview Questions that are generally asked in any CICS Interview in MNCs
Q1 - What is MDT ?
Ans - Bit in the attribute byte indicating modification of field on screen.If the user keys in any data into the field, it turns the MDT ON indicating that the data is modified. To save transmission time , 3270 terminal sends a field over the TC line only if the MDT is on. Otherwise, the field value is not transmitted.
Q2 - What is DFHCOMMAREA ?
Ans - DFHCOMMAREA in the Linkage section is used to pass the data in working storage commarea from one to program to another program. It should be defined with as at least one byte long. As the working storage section is freshly allocated for every execution.
Q3- What is Execution Interface Block (EIB) ?Ans - EIB is a CICS area that contains information related to the current task, which can be used for debugging the program. The most widely used variables are EIBDATE, EIBTIME, EIBAID, EIBCALEN, EIBCPOSN, EIBRESP, EIBRSRCE (resource), EIBFN (recent CICS command code), EIBTRMID and EIBTRNID.
Q4- What are the important tables used in the CICS-DB2 environment ?Ans - CICS manages it's communication with DB2 with special interface modules called CICS/DB2 Attachment Facility. When a CICS program issues a SQL statement, CICS requests the attachment facility to establish a connection with DB2 called a thread. The information about the CICS transaction and DB2 is entered in Resource Control Table (RCT). The plan information is referenced through the RCT Entries.
Q5- What are the various commands used to browse through a dataset ?Ans - STARTBR, READNEXT, READPREV and RESETBR. The options used are DATASET, RIDFLD, RRN/RBA, GENERIC, and KEYLENGTH for the 3 commands, and INTO, LENGTH for READNEXT and READPREV command, and EQUAL/GTEQ for STARTBR only. RESP can be used with any. ENDBR is used to end the browse operation
Q6- What is 2 phase commit ?Ans - It occurs when a programmer Issue's an Exec CICS Syncpoint command. This is called a two phase Commit because CICS will first commit changes to the resources under its control like VSAM files, before DB2 changes are committed. Usually CICS signals DB2 to complete the next phase and release all the locks.
Q7- What are ASRA,AICA,AEY9 abend ?Ans - ASRA - Any data exception problem SOC7, SOC4 etc
AICA - Runaway Task.
AEY9 - DB2/IDMS Database is not up.
Q8 What are the differences between TSQ and a TDQ ?
Ans –
(1) In Temporary Storage Queues Data is read randomly, While in Transient Data Queues data must be read sequentially.
(2) In a TSQ data can be read any number of times as it remains in the queue until the entire Queue is deleted. In TDQ data item can be read once only. To reuse the TDQ it must be closed and reopened.
(3) Data can be changed in TSQ, but not in TDQ.
(4) TSQ can be written to Auxiliary or Main Storage, while TDQ is written to Disk. Temporary storage is a holding place, while Transient data is always associated with destination. The
(5) TSQ name is defined dynamically, while a TDQ name need to be defined in the DCT. Note: An application uses TSQ 's to pass info' from task to task, while a TDQ to accumulate records before processing or send data for external use, such as a print operation or other.
Q9- What are Extra partition & Intra partition TDQs ?Ans - Extra-partition TDQ's are datasets used for communication between CICS and other CICS/Batch regions. Intra-partition TDQ's are queues for communication within CICS region. CICS stores the Intra-partition TDQ in a dataset 'DFHNTRA' on the Disk. Extra-partition TDQ doesn't have to be a disk file, it can reside on any device that's a valid QSAM/VSAM. The DCT entry contains the destination-Id, type of TDQ, Destination, Trigger level if needed
Q10 How is an Abend handled in a CICS program ?Ans - The HANDLE ABEND command is used to trap and Handle errors. It has 4 possible options and only one of them can be used with this command at a time. The options are Program(...) to transfer control to the program, Label(...) to transfer control to the specified paragraph, Cancel option keeps the earlier Handle Abends from being executed. Reset option will reactivate the Handle Abend commands, which were previously cancelled.
Q11 What is Quasi-reentrancy ?Ans - There are times when many users are concurrently using the same program, this is what we call Multi-Threading. For example, 50 users are using program A, CICS will provide 50 Working storage for that program but one Procedure Division. And this technique is known as quasi-reentrancy.
Q1 - What is MDT ?
Ans - Bit in the attribute byte indicating modification of field on screen.If the user keys in any data into the field, it turns the MDT ON indicating that the data is modified. To save transmission time , 3270 terminal sends a field over the TC line only if the MDT is on. Otherwise, the field value is not transmitted.
Q2 - What is DFHCOMMAREA ?
Ans - DFHCOMMAREA in the Linkage section is used to pass the data in working storage commarea from one to program to another program. It should be defined with as at least one byte long. As the working storage section is freshly allocated for every execution.
Q3- What is Execution Interface Block (EIB) ?Ans - EIB is a CICS area that contains information related to the current task, which can be used for debugging the program. The most widely used variables are EIBDATE, EIBTIME, EIBAID, EIBCALEN, EIBCPOSN, EIBRESP, EIBRSRCE (resource), EIBFN (recent CICS command code), EIBTRMID and EIBTRNID.
Q4- What are the important tables used in the CICS-DB2 environment ?Ans - CICS manages it's communication with DB2 with special interface modules called CICS/DB2 Attachment Facility. When a CICS program issues a SQL statement, CICS requests the attachment facility to establish a connection with DB2 called a thread. The information about the CICS transaction and DB2 is entered in Resource Control Table (RCT). The plan information is referenced through the RCT Entries.
Q5- What are the various commands used to browse through a dataset ?Ans - STARTBR, READNEXT, READPREV and RESETBR. The options used are DATASET, RIDFLD, RRN/RBA, GENERIC, and KEYLENGTH for the 3 commands, and INTO, LENGTH for READNEXT and READPREV command, and EQUAL/GTEQ for STARTBR only. RESP can be used with any. ENDBR is used to end the browse operation
Q6- What is 2 phase commit ?Ans - It occurs when a programmer Issue's an Exec CICS Syncpoint command. This is called a two phase Commit because CICS will first commit changes to the resources under its control like VSAM files, before DB2 changes are committed. Usually CICS signals DB2 to complete the next phase and release all the locks.
Q7- What are ASRA,AICA,AEY9 abend ?Ans - ASRA - Any data exception problem SOC7, SOC4 etc
AICA - Runaway Task.
AEY9 - DB2/IDMS Database is not up.
Q8 What are the differences between TSQ and a TDQ ?
Ans –
(1) In Temporary Storage Queues Data is read randomly, While in Transient Data Queues data must be read sequentially.
(2) In a TSQ data can be read any number of times as it remains in the queue until the entire Queue is deleted. In TDQ data item can be read once only. To reuse the TDQ it must be closed and reopened.
(3) Data can be changed in TSQ, but not in TDQ.
(4) TSQ can be written to Auxiliary or Main Storage, while TDQ is written to Disk. Temporary storage is a holding place, while Transient data is always associated with destination. The
(5) TSQ name is defined dynamically, while a TDQ name need to be defined in the DCT. Note: An application uses TSQ 's to pass info' from task to task, while a TDQ to accumulate records before processing or send data for external use, such as a print operation or other.
Q9- What are Extra partition & Intra partition TDQs ?Ans - Extra-partition TDQ's are datasets used for communication between CICS and other CICS/Batch regions. Intra-partition TDQ's are queues for communication within CICS region. CICS stores the Intra-partition TDQ in a dataset 'DFHNTRA' on the Disk. Extra-partition TDQ doesn't have to be a disk file, it can reside on any device that's a valid QSAM/VSAM. The DCT entry contains the destination-Id, type of TDQ, Destination, Trigger level if needed
Q10 How is an Abend handled in a CICS program ?Ans - The HANDLE ABEND command is used to trap and Handle errors. It has 4 possible options and only one of them can be used with this command at a time. The options are Program(...) to transfer control to the program, Label(...) to transfer control to the specified paragraph, Cancel option keeps the earlier Handle Abends from being executed. Reset option will reactivate the Handle Abend commands, which were previously cancelled.
Q11 What is Quasi-reentrancy ?Ans - There are times when many users are concurrently using the same program, this is what we call Multi-Threading. For example, 50 users are using program A, CICS will provide 50 Working storage for that program but one Procedure Division. And this technique is known as quasi-reentrancy.
IBM mainframes COBOL qsam/vsam FILE STATUS CODES
Hi Friends
IBM mainframes COBOL qsam/vsam FILE STATUS CODES are available .Please check the Link for the latest codes and File Status
http://publib.boulder.ibm.com/cgi-bin/bookmgr/BOOKS/igy3lr00/6.1.8.9.1?SHELF=igy3sh00&DT=20011206182158#HDRSTATKEY
IBM mainframes COBOL qsam/vsam FILE STATUS CODES are available .Please check the Link for the latest codes and File Status
http://publib.boulder.ibm.com/cgi-bin/bookmgr/BOOKS/igy3lr00/6.1.8.9.1?SHELF=igy3sh00&DT=20011206182158#HDRSTATKEY
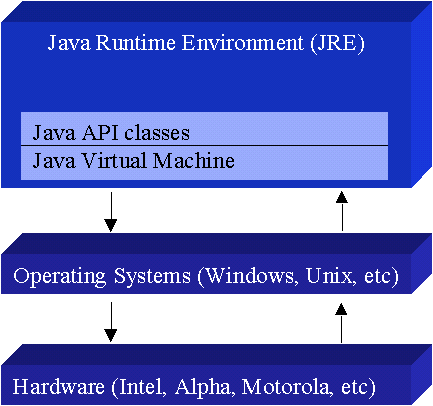
Working of Java Virtual Machine (JVM)
JVM(Java virtual machine):it is the runtime environment for java programs and it contains the following :
1)class loader
2)byte code verifier
3)jit compiler and interpreter
java is a platform independent language which means it can be operated in any operating system
when you execute a program in C && C++ a .exe file is obtained which contains the source code
and operating system details where as when you execute a program in java a .class file is created which contains the byte code(source code) only.It is the JVM which links this byte code with the operating system details.
The Java Virtual Machine forms part of a large system, the Java Runtime Environment (JRE). Each operating system and CPU architecture requires a different JRE. The JRE comprises a set of base classes, which are an implementation of the base Java API, as well as a JVM. The portability of Java comes from implementations on a variety of CPUs and architectures. Without an available JRE for a given environment, it is impossible to run Java software.
1)class loader
2)byte code verifier
3)jit compiler and interpreter
java is a platform independent language which means it can be operated in any operating system

when you execute a program in C && C++ a .exe file is obtained which contains the source code
and operating system details where as when you execute a program in java a .class file is created which contains the byte code(source code) only.It is the JVM which links this byte code with the operating system details.
The Java Virtual Machine forms part of a large system, the Java Runtime Environment (JRE). Each operating system and CPU architecture requires a different JRE. The JRE comprises a set of base classes, which are an implementation of the base Java API, as well as a JVM. The portability of Java comes from implementations on a variety of CPUs and architectures. Without an available JRE for a given environment, it is impossible to run Java software.
Functionality of JVM(Java Virtual Machine)
Java sovles the problem of platform independence by usingbyte code.Java complier does not produce native executablecode.
Instead it produces a special format called byte code.Byte code is a highly optimized set of instructionsdesigned to executed by a java runtime system called JavaVirtual Machine(JVM).JVM is an interpreter for byte code.
This interpreter reads or understands the bytecode andexecutes the corresponding native machine instructions.Thus to port java programs to a new platform ,all thatneeded is to port the interperter and some of the libraryroutines.
Even the complier is written in java.The bytecodes are precisely defined and remain the same on allplatforms.The use of byte code enables the java runtime system toexecute programs much faster.
The JVM is the core of the Java platform and is responsible for:
1. Loading bytecodes from the class files
2. Verifying the loaded byte codes
3. Linking the program with the necessary libraries
4. Memory Management by Garbage Collection
5. Managing calls between the program and the host environment.
Instead it produces a special format called byte code.Byte code is a highly optimized set of instructionsdesigned to executed by a java runtime system called JavaVirtual Machine(JVM).JVM is an interpreter for byte code.
This interpreter reads or understands the bytecode andexecutes the corresponding native machine instructions.Thus to port java programs to a new platform ,all thatneeded is to port the interperter and some of the libraryroutines.
Even the complier is written in java.The bytecodes are precisely defined and remain the same on allplatforms.The use of byte code enables the java runtime system toexecute programs much faster.
The JVM is the core of the Java platform and is responsible for:
1. Loading bytecodes from the class files
2. Verifying the loaded byte codes
3. Linking the program with the necessary libraries
4. Memory Management by Garbage Collection
5. Managing calls between the program and the host environment.
Login Authentication using JSP, Servlet, MySQL in JAVA
In this example we will show you how to authenticate and login user against database username and password. This program consists of a JSP page and a Servlet to authenticate the user against database username and password.
User enters the username and password on the JSP page and clicks on the "Sign-In" button. On the form submit event, data is posted to the servlet for authenticating the user. Servlet makes JDBC connection and authenticate the user. Before submitting data to servlet, javascript is ensuring that none of the fields must be empty.
We are using tomcat server for running Servlet and JSP page. You can use any browser to test the application. We are using two files AuthenticLogin.jsp and LoginAuthentication.java and we are making the application in "webapps/JSPMultipleForms" in tomcat server.
Download Source Code
User enters the username and password on the JSP page and clicks on the "Sign-In" button. On the form submit event, data is posted to the servlet for authenticating the user. Servlet makes JDBC connection and authenticate the user. Before submitting data to servlet, javascript is ensuring that none of the fields must be empty.
We are using tomcat server for running Servlet and JSP page. You can use any browser to test the application. We are using two files AuthenticLogin.jsp and LoginAuthentication.java and we are making the application in "webapps/JSPMultipleForms" in tomcat server.
Download Source Code
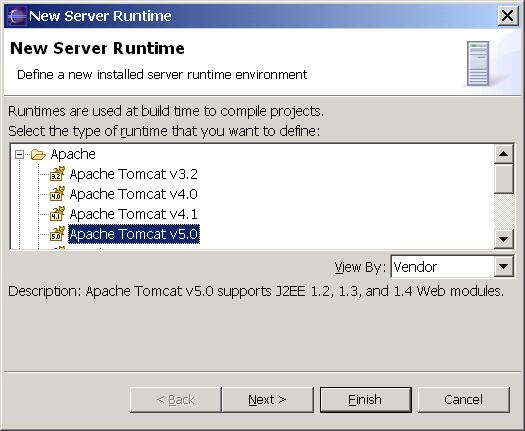
Installing Apache Tomcat Server in Eclipse IDE
- If you do not have Apache Tomcat on your machine, you will first need to download and unzip Apache Tomcat (this scenario was written using Apache Tomcat version 5.0.28, but other versions can be substituted).
- Start the Eclipse WTP workbench.
- Open Window -> Preferences -> Server -> Installed Runtimes to create a Tomcat installed runtime.
- Click on Add... to open the New Server Runtime dialog, then select your runtime under Apache (Apache Tomcat v5.0 in this example):
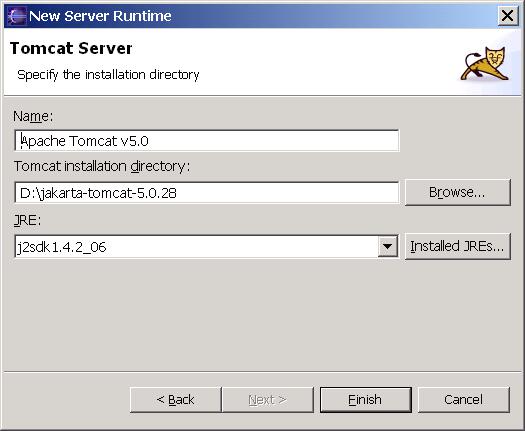
- Click Next , and fill in your Tomcat installation directory :
- Ensure the selected JRE is a full JDK and is of a version that will satisfy Apache Tomcat (this scenario was written using SUN JDK 1.4.2_06). If necessary, you can click on Installed JREs... to add JDKs to Eclipse.
- Click Finish .
What is the difference between JRE,JVM and JDK?
JDK (Java Development Kit)
Java Developer Kit contains tools needed to develop the Java programs, and JRE to run the programs. The tools include compiler (javac.exe), Java application launcher (java.exe), Appletviewer, etc…Compiler converts java code into byte code. Java application launcher opens a JRE, loads the class, and invokes its main method.
You need JDK, if at all you want to write your own programs, and to compile the m. For running java programs, JRE is sufficient.
JRE is targeted for execution of Java files
i.e. JRE = JVM + Java Packages Classes(like util, math, lang, awt,swing etc)+runtime libraries.
JDK is mainly targeted for java development. I.e. You can create a Java file (with the help of Java packages), compile a Java file and run a java file
JRE (Java Runtime Environment)
Java Runtime Environment contains JVM, class libraries, and other supporting files. It does not contain any development tools such as compiler, debugger, etc. Actually JVM runs the program, and it uses the class libraries, and other supporting files provided in JRE. If you want to run any java program, you need to have JRE installed in the systemThe Java Virtual Machine provides a platform-independent way of executing code; programmers can concentrate on writing software, without having to be concerned with how or where it will run.
If u just want to run applets (ex: Online Yahoo games or puzzles), JRE needs to be installed on the machine.
JVM (Java Virtual Machine)
As we all aware when we compile a Java file, output is not an 'exe' but it's a '.class' file. '.class' file consists of Java byte codes which are understandable by JVM. Java Virtual Machine interprets the byte code into the machine code depending upon the underlying operating system and hardware combination. It is responsible for all the things like garbage collection, array bounds checking, etc… JVM is platform dependent.The JVM is called "virtual" because it provides a machine interface that does not depend on the underlying operating system and machine hardware architecture. This independence from hardware and operating system is a cornerstone of the write-once run-anywhere value of Java programs.
There are different JVM implementations are there. These may differ in things like performance, reliability, speed, etc. These implementations will differ in those areas where Java specification doesn’t mention how to implement the features, like how the garbage collection process works is JVM dependent, Java spec doesn’t define any specific way to do this.
There Are No Famous Programmers
I frequently meet a friend for lunch and we talk. Usually I'll blab on and on about music, or some weirdo project I have going on. He'll tell me about jobs he's had or trips he might take now that he's sold a company and can chill out for a while. After one such meeting he said, "It's so refreshing to meet up with a geek who doesn't talk about VCs and term sheets the whole time."
Let's try an experiment. Think of a project you use all day. Maybe it's Rails or Python or something. Now, name 4 people on the core team without looking them up. I can't do that for anything I use. Alright, let's say you can do that. You know a myriad of things about the people who make your tools, but can you honestly say you know as much about them as you do about the tools they made you? Be honest with yourself and really look at how much you know about the people behind your gear as you do about the gear itself.
The famous programmers aren't really famous for programming anymore, but instead because they created some business or non-profit. Their code can't stand on its own as awesome, it has to be paired with some non-code fame formation and then people can grok their concept.
This is why I believe that there are no famous programmers, and being famous does not help you in your programming career. I've said this before, but today I was offered a system administrator job, again. It was very humbling to say the least. It kind of knocked me out to have someone think through all the things their company needs and the only thing they could think I'd be good at was system administration.
Yep, just a system administrator. Still.
Let's try an experiment. Think of a project you use all day. Maybe it's Rails or Python or something. Now, name 4 people on the core team without looking them up. I can't do that for anything I use. Alright, let's say you can do that. You know a myriad of things about the people who make your tools, but can you honestly say you know as much about them as you do about the tools they made you? Be honest with yourself and really look at how much you know about the people behind your gear as you do about the gear itself.
The famous programmers aren't really famous for programming anymore, but instead because they created some business or non-profit. Their code can't stand on its own as awesome, it has to be paired with some non-code fame formation and then people can grok their concept.
This is why I believe that there are no famous programmers, and being famous does not help you in your programming career. I've said this before, but today I was offered a system administrator job, again. It was very humbling to say the least. It kind of knocked me out to have someone think through all the things their company needs and the only thing they could think I'd be good at was system administration.
Yep, just a system administrator. Still.
In Depth: Ubuntu: meritocracy not democracy
Ubuntu has many recognisable traits, but one of the best is its reputation for working with its community.
Since Mark Shuttleworth forged the original team in 2004, the Ubuntu community has exploded in size, spawning a diverse range of teams across the globe.
Underlining this sense of community was Mark's eagerness to embrace transparency, putting in place open governance and tools, a code of conduct and an invitation for volunteers to join the ranks of the project.
Recently, however, there was some controversy surrounding this community ethos. It kicked off when Canonical, Ubuntu's primary sponsor, announced a refreshed brand for the project. A new lick of paint was applied to the logo, wallpaper and more, and new colour schemes, textures, photographic treatments and other artistic flourishes were shared with the wider community.
As part of the brand development, key members of the community were flown to London to work with the design team, and senior community governance boards were told about the brand before it was publicly announced.
Source:http://feedproxy.google.com/~r/techradar/allnews/~3/xeF2BjFVais/story01.htm
Since Mark Shuttleworth forged the original team in 2004, the Ubuntu community has exploded in size, spawning a diverse range of teams across the globe.
Underlining this sense of community was Mark's eagerness to embrace transparency, putting in place open governance and tools, a code of conduct and an invitation for volunteers to join the ranks of the project.
Recently, however, there was some controversy surrounding this community ethos. It kicked off when Canonical, Ubuntu's primary sponsor, announced a refreshed brand for the project. A new lick of paint was applied to the logo, wallpaper and more, and new colour schemes, textures, photographic treatments and other artistic flourishes were shared with the wider community.
As part of the brand development, key members of the community were flown to London to work with the design team, and senior community governance boards were told about the brand before it was publicly announced.
Source:http://feedproxy.google.com/~r/techradar/allnews/~3/xeF2BjFVais/story01.htm
uTorrent For Linux Is Coming, Finally
Five years after uTorrent was released for the Windows platform the development team has announced that it’s working on a Linux version of the torrent client. The massive demand from users is cited as one of the main reasons why Linux users will have a native uTorrent application this coming summer
uTorrent for Windows saw its first public release in September 2005 and soon became the most widely used BitTorrent application. Every month, more than 50 million people use uTorrent and this number continues to grow alongside BitTorrent’s ever-increasing user base.
Ever since uTorrent was released, Mac and Linux users have begged the developers to release a version of the client designed to work on their computers. In 2006, when uTorrent was sold to BitTorrent Inc., the company announced that a Mac version was coming. In 2008, nearly two years after the announcement, it was finally released to the public.
With the the release of the Mac version, Linux users were the only ones left out in the cold, but this is about to change. The uTorrent development team has just announced that they are working on a Linux version of the client. Further details on the time line and an eventual release date are not available at the moment.
Source: www.torrentfreak.com
uTorrent for Windows saw its first public release in September 2005 and soon became the most widely used BitTorrent application. Every month, more than 50 million people use uTorrent and this number continues to grow alongside BitTorrent’s ever-increasing user base.
Ever since uTorrent was released, Mac and Linux users have begged the developers to release a version of the client designed to work on their computers. In 2006, when uTorrent was sold to BitTorrent Inc., the company announced that a Mac version was coming. In 2008, nearly two years after the announcement, it was finally released to the public.
With the the release of the Mac version, Linux users were the only ones left out in the cold, but this is about to change. The uTorrent development team has just announced that they are working on a Linux version of the client. Further details on the time line and an eventual release date are not available at the moment.
Source: www.torrentfreak.com
How to Configure a VNC Server in Linux
Step 1
Find out if VNC is already installed on your Linux distro. Users of Ubuntu and Fedora, two of the more common distros, already have VNC servers installed and don’t need to install anything.
Not running one of these two mainstream distros? Run a search in your distro’s package manager for VNC clients—if you’re running Gnome, look for “vinagre”; if you’re running KDE look for “kfrb.” If the packages aren’t already installed, install them using your distro’s tools.
Step 2
Configure VNC. How to do this varies depending on which desktop you’re using. Gnome users can click “System,” then “Preferences,” then “Remote Desktop,” to bring up the configuration window; KDE users should click “System Settings,” then “Sharing,” then “Desktop Sharing,” then “Configure,” to bring up the dialogue. Allow users to see your desktop by clicking the appropriate box and then adding a password.
Step 3
Test the configuration. Using another computer on the network, attempt to connect to your IP with a VNC client by entering the computer’s IP address (find the IP address by typing “ifconfig” at a terminal.) If all went well, the desktop of the computer with the server installed should pop up as expected. Congratulations!
Find out if VNC is already installed on your Linux distro. Users of Ubuntu and Fedora, two of the more common distros, already have VNC servers installed and don’t need to install anything.
Not running one of these two mainstream distros? Run a search in your distro’s package manager for VNC clients—if you’re running Gnome, look for “vinagre”; if you’re running KDE look for “kfrb.” If the packages aren’t already installed, install them using your distro’s tools.
Step 2
Configure VNC. How to do this varies depending on which desktop you’re using. Gnome users can click “System,” then “Preferences,” then “Remote Desktop,” to bring up the configuration window; KDE users should click “System Settings,” then “Sharing,” then “Desktop Sharing,” then “Configure,” to bring up the dialogue. Allow users to see your desktop by clicking the appropriate box and then adding a password.
Step 3
Test the configuration. Using another computer on the network, attempt to connect to your IP with a VNC client by entering the computer’s IP address (find the IP address by typing “ifconfig” at a terminal.) If all went well, the desktop of the computer with the server installed should pop up as expected. Congratulations!
Instruction on how install Perl DBD on IBM AIX 5.3 Unix
It is challenging to install perl DBD on IBM AIX. There are several different ways to install and compile Perl DBD on AIX. Definitely check out the REAME file. I have tried many different ways, and the following steps actually got me through the complete installation without error.
First you need to install Perl and DBI. When setting environment variables, you should update the following according to your path.
Set the following environment variables:
export PATH=$PATH:/usr/vacpp/bin
export ORACCENV='cc=xlc_r'
export LIBPATH=$LIBPATH:/a01/oracle/lib32:/usr/ccs/lib
export LD_RUN_PATH=/a01/oracle/lib32:/usr/ccs/lib
Run the following commands:
cpan
install T/TI/TIMB/DBI-1.53.tar.gz
cpan
look P/PY/PYTHIAN/DBD-Oracle-1.22.tar.gz
perl Makefile.PL -nob
Run as root:
ln -s /usr/lib /lib32
export ORACLE_USERID=oracle_user/oracle_password@ccbprd
perl Makefile.PL -m $ORACLE_HOME/rdbms/demo/demo_rdbms32.mk
perl -p -i -e 's/-q32//g' Makefile
make test
Now, if everything OK, run:
make install
First you need to install Perl and DBI. When setting environment variables, you should update the following according to your path.
Set the following environment variables:
export PATH=$PATH:/usr/vacpp/bin
export ORACCENV='cc=xlc_r'
export LIBPATH=$LIBPATH:/a01/oracle/lib32:/usr/ccs/lib
export LD_RUN_PATH=/a01/oracle/lib32:/usr/ccs/lib
Run the following commands:
cpan
install T/TI/TIMB/DBI-1.53.tar.gz
cpan
look P/PY/PYTHIAN/DBD-Oracle-1.22.tar.gz
perl Makefile.PL -nob
Run as root:
ln -s /usr/lib /lib32
export ORACLE_USERID=oracle_user/oracle_password@ccbprd
perl Makefile.PL -m $ORACLE_HOME/rdbms/demo/demo_rdbms32.mk
perl -p -i -e 's/-q32//g' Makefile
make test
Now, if everything OK, run:
make install
VB.NET Crystal Reports Formula Fields
If you have a Crystal Reports with Qty and Price , you need an additional field in your Crystal Reports for the Total of QTY X PRICE . In this situation you have to use the Formula Field in Crystal Reports.
In this tutorial we are showing the all orders with qty and price and the total of each row , that means each in each row we are showing the total of qty and price. Before starting this tutorial.
Create a new Crystal Reports with fields CustomerName , Order Date , Product Name and Product Price . If you do not know how to create this report , just look the previous tutorial Crystal Report from multiple tables . In that report selecting only four fields , here we need one more field Prodcut->Price .
After you create the Crystal Reports you screen is look like the following picture :
Next is to create the a Formula Field for showing the total of Qty and Price .
Right Click Formula Field in the Field Explorer and click New. Then you will get an Input Message Box , type Total in textbox and click Use Editor
Now you can see Formula Editor screen . Now you can enter which formula you want . Here we want the result of Qty X Price . For that we select OrderDetails.Qty , the multiplication operator and Product.Price . Double click each field for selection.
Now you can see Total Under the Formula Field . Drag the field in to the Crystal Reports where ever you want .
Now the designing part is over . Select the default form (Form1.vb) you created in VB.NET and drag a button and CrystalReportViewer control to your form.
How to Create a Formula in Crystal Reports XI,VB.NET Crystal Reports Formula Fields
Formulas serve many purposes and in my example I am going to show you how I am able to combine to fields from a database to create one complete field. This How-To assumes that you have worked through my previous How-To article of creating a simple report. It is this simple report I am going to use.
- Open Crystal Reports XI
- Step 2Open the simple report you created rfom my previous how-to article.
- Step 3
 Right clickOn the field explorer, right click on Formula Fields.
Right clickOn the field explorer, right click on Formula Fields.
- Step 4
 NewSelect "New" from the popup menu.
NewSelect "New" from the popup menu.
- Step 5
 FullNameGive your formula the name, "FullName".
FullNameGive your formula the name, "FullName".
- Step 6
 OkClick the ok button.
OkClick the ok button.
- Step 7
 ExpandThe formula workshop window will appear. In here we are going to combine the last name database field, with the first name database field to create the formula "FullName." Expand the window that displays the database fields by clicking on the [+] plus sign. See image.
ExpandThe formula workshop window will appear. In here we are going to combine the last name database field, with the first name database field to create the formula "FullName." Expand the window that displays the database fields by clicking on the [+] plus sign. See image.
- Step 8
 Get LastNameDouble click the "LastName" field. This will put it in the formula editor area.
Get LastNameDouble click the "LastName" field. This will put it in the formula editor area.
- Step 9
 ConcatenateAdd the amerpsand (&) symbol and then in quotations a comma followed by a space and then another ampersand. See the picture for how it looks. This will help separate the last name from the first name with a comma. The ampersand symbols concatenates two strings together.
ConcatenateAdd the amerpsand (&) symbol and then in quotations a comma followed by a space and then another ampersand. See the picture for how it looks. This will help separate the last name from the first name with a comma. The ampersand symbols concatenates two strings together.
- Step 10
 Get FirstnameDouble click on the first name field to add it to the formula editor.
Get FirstnameDouble click on the first name field to add it to the formula editor.
- Step 11
 Check for ErrorsCheck to make sure the formula does not have any errors in it by clicking the (x+2) button with the green checkmark underneath.
Check for ErrorsCheck to make sure the formula does not have any errors in it by clicking the (x+2) button with the green checkmark underneath.
- Step 12
 No ErrorsYou will should receive the message box as shown in the picture. If you receive a different message it means there is an error. Go back through the steps, follow the pictures and try again before you continue.
No ErrorsYou will should receive the message box as shown in the picture. If you receive a different message it means there is an error. Go back through the steps, follow the pictures and try again before you continue.
- Step 13
 Save and CloseClick the "Save and Close" button.
Save and CloseClick the "Save and Close" button.
- Step 14
 Formula CreatedThe formula has been created and exists in the Field Explorer window as shown in the picture.
Formula CreatedThe formula has been created and exists in the Field Explorer window as shown in the picture.
- Step 15
 Formula added to reportAdd the formula to the report by double clicking the formula name, dragging your mouse to the report and clicking the mouse button to drop it in the details section. Your report should now look like the picture.
Formula added to reportAdd the formula to the report by double clicking the formula name, dragging your mouse to the report and clicking the mouse button to drop it in the details section. Your report should now look like the picture.
- Step 16
 Final ReportPress the "F5" key to see how the report with the formula looks. Click the Ok button if you get the message box asking if you wish to refresh the data. The picture shows the final results.
Final ReportPress the "F5" key to see how the report with the formula looks. Click the Ok button if you get the message box asking if you wish to refresh the data. The picture shows the final results.
How to Create Hypertext Link to open them in default browser in In VB .NET?
This is pretty simple :). First add a linklabel to your form (or a textbox/label/etc.), and create a click event for that label. In the event, use this code to open up the url:
Process.Start( Path (As String) )
for example
Process.Start( "http://developers-arena.blogspot.com" )
would open up yahoo answers in the default web browser. You can also use this to navigate to file locations. You don't have to use a link label (you can just use the Process.Start() function anywhere in the program), but it's the neater way to provide a link to click
Process.Start( Path (As String) )
for example
Process.Start( "http://developers-arena.blogspot.com" )
would open up yahoo answers in the default web browser. You can also use this to navigate to file locations. You don't have to use a link label (you can just use the Process.Start() function anywhere in the program), but it's the neater way to provide a link to click
VB.NET how to run at startup?
First of all this is very complex programming. so if you not know what you doing don't try this ( you might have to reinstall windows after this ) and i have not tried this before so im not even sure this works correct
you should replace this register value with the path to your program
Key :
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\… NT\CurrentVersion\Winlogon
Value :Shell
(default value is explorer.exe)
then your program should run after user longin
winlogon.exe ( one that ask for username and password ) will run the program on that reg value after user enter correct username and password.
before your program exit it should run explorer.exe (other wise you not get explorer in screen)
Note : i tryed to replace winlogon.exe ones and had to reinstall windows. so be ready to install windows if this not work.
im not sure how much memory is available at that stage (in my case with winlogon i was not able to load a nother program at that stage and got a "not enough memory " ).
you should replace this register value with the path to your program
Key :
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\… NT\CurrentVersion\Winlogon
Value :Shell
(default value is explorer.exe)
then your program should run after user longin
winlogon.exe ( one that ask for username and password ) will run the program on that reg value after user enter correct username and password.
before your program exit it should run explorer.exe (other wise you not get explorer in screen)
Note : i tryed to replace winlogon.exe ones and had to reinstall windows. so be ready to install windows if this not work.
im not sure how much memory is available at that stage (in my case with winlogon i was not able to load a nother program at that stage and got a "not enough memory " ).
How to create a moving a pictureBox right till it hits another PixelBox in VB.net?
Im trying to make a ball move from the left side of the form to the right until it hits another PixelBox can any one suggest how to do it?
Answer:
Well, the first step is getting the ball to move, at a steady pace. So to do this we will use the timer control, click and drag a timer onto the form, then set the interval property to 100 or so (depending on how fast you want the ball to move). Then make sure it is enabled, and double click on it to create the tick event. In the tick event:
ball.Left = ball.Left + 1
Depending on how fast you want it to go, change the number one to something higher (the smaller this number the smoother the movement, it's better to put the timer interval down lower, if you want speed). Then we want to check if this new move means it's hit the other picture box, so right after moving it:
If ball.Left + ball.Width > otherpicturebox.Left And ball.Top + ball.Height > otherpicturebox.Top And ball.Left < otherpicturebox.Left + otherpicturebox.Width And ball.Top < otherpicturebox.Top + otherpicturebox.Height Then
Timer1.Enabled = False
MsgBox("I've hit the other picture box")
End If
Answer:
Well, the first step is getting the ball to move, at a steady pace. So to do this we will use the timer control, click and drag a timer onto the form, then set the interval property to 100 or so (depending on how fast you want the ball to move). Then make sure it is enabled, and double click on it to create the tick event. In the tick event:
ball.Left = ball.Left + 1
Depending on how fast you want it to go, change the number one to something higher (the smaller this number the smoother the movement, it's better to put the timer interval down lower, if you want speed). Then we want to check if this new move means it's hit the other picture box, so right after moving it:
If ball.Left + ball.Width > otherpicturebox.Left And ball.Top + ball.Height > otherpicturebox.Top And ball.Left < otherpicturebox.Left + otherpicturebox.Width And ball.Top < otherpicturebox.Top + otherpicturebox.Height Then
Timer1.Enabled = False
MsgBox("I've hit the other picture box")
End If
How do you make a VB.NET GUI program that is not a square
Unlike as in VB6, where you have to use the API to create a translucent or transparent form, you only need one line of code to do so in VB.NET. Specifically, all you have to do is set the opacity property of the form to the desired value.
Private Sub Form1_Load(ByVal sender As System.Object, _
ByVal e As System.EventArgs) Handles MyBase.Load
Me.Opacity = 0.5
End Sub
Private Sub Form1_Load(ByVal sender As System.Object, _
ByVal e As System.EventArgs) Handles MyBase.Load
Me.Opacity = 0.5
End Sub
Advantages and disadvantages of a mainframe computer
The advantages boil down to redundancy and capacity.
If your typical PC is a pickup truck, able to carry a small load of bricks, then you could think of the mainframe as a WHOLE FLEET of commercial dump trucks, each able to carry many pickup-loads of bricks. The redundancy is built in to maximize uptime and reliability. If you need to move huge quantities of bricks, it doesn't matter much if one or two dump trucks (in your large fleet of dump trucks) break, or go down for maintenance...the bricks keep moving.
Essentially, mainframes can process MASSIVE amounts of information (compared to mini computers or micro computers / PCs), and do it very reliably.
The disadvantage of mainframes? Cost of hardware, special operating systems/software (more cost there, too). You typically won't see a mainframe used unless some organization with really deep pockets has a mission-critical function that requires massive amounts of information to be processed, in a very reliable manner.
If your typical PC is a pickup truck, able to carry a small load of bricks, then you could think of the mainframe as a WHOLE FLEET of commercial dump trucks, each able to carry many pickup-loads of bricks. The redundancy is built in to maximize uptime and reliability. If you need to move huge quantities of bricks, it doesn't matter much if one or two dump trucks (in your large fleet of dump trucks) break, or go down for maintenance...the bricks keep moving.
Essentially, mainframes can process MASSIVE amounts of information (compared to mini computers or micro computers / PCs), and do it very reliably.
The disadvantage of mainframes? Cost of hardware, special operating systems/software (more cost there, too). You typically won't see a mainframe used unless some organization with really deep pockets has a mission-critical function that requires massive amounts of information to be processed, in a very reliable manner.
What are the intrinsic objects present in ASP.NET
Many features of ASP.NET will be familiar to you if you have used previous versions of ASP. Although the object-oriented design and underlying code of ASP.NET is radically different from ASP, many of the most commonly used keywords and operators in ASP remain in ASP.NET. Familiar intrinsic objects such as Request, Response, Server, Application, and Session are part of ASP.NET and are used in much the same way as they were in ASP. However, in ASP.NET these objects are defined in new classes in the System.Web namespace. For example, these intrinsic objects are now properties of the System.Web.HttpContext class but because the objects are automatically created by ASP.NET when a new request for a Web resource is received and a new context is created, you can use them directly
without having to instantiate new objects.
Request,Response,Application,Server and Session are the intrensic obejects in ASP.Net
without having to instantiate new objects.
Request,Response,Application,Server and Session are the intrensic obejects in ASP.Net
How to find real memory in IBM AIX Unix,Commands to find real memory in IBM AIX
To display real memory in kilobytes (KB), run either one of the following commands:
bootinfo -r
lsattr -El sys0 -a realmem
bootinfo -r
lsattr -El sys0 -a realmem
How to Convert IBM As400 Spool Files to Word or Excel
1.Perform your mainframe database query as Normally.
2.Generate your spool file . When saving the file, use the CPYTOIMPF command to get the output as a comma separated value file (Extension of *.csv).
3.Open MS Word or MS Excel.
4.Open the .csv file in Excel or Word.
5. Click “Yes” on the “Convert To Table” dialog box. This will separate all the values in the spool file separated by commas into their own cells in Excel, or into their own table cells in MS Word.
2.Generate your spool file . When saving the file, use the CPYTOIMPF command to get the output as a comma separated value file (Extension of *.csv).
3.Open MS Word or MS Excel.
4.Open the .csv file in Excel or Word.
5. Click “Yes” on the “Convert To Table” dialog box. This will separate all the values in the spool file separated by commas into their own cells in Excel, or into their own table cells in MS Word.
History of the IBM Mainframes Computer
Mainframes are powerful computers used mainly by large organizations for critical applications, typically bulk data processing such as census, industry and consumer statistics, enterprise resource planning, and financial transaction processing.
A mainframe is a continually evolving general purpose computing platform incorporating in it architectural definition the essential functionality required by its target applications."
Some additional comments about this definition are in order. One of the most fundamental features of the mainframe world is the rapid and apparently endless evolution of the product line. From 16 general and 4 floating point registers of System/360, to the control register additions in the early 370s, to the access registers of the latter 370s, to the full complement of floating point registers of System/390 and the full 64 bit implementation offered by the z800/900 models; from 6 selector channels to 16 block multiplexing channels to 256 high speed optical channels; from 142 instructions to over 500 instructions; from real addressing to virtual addressing to virtual machines; from the simple 8 bit memory of the 360/30 through generations of development to the multiported, multilevel caching, multiprocessor supporting memory of the z900, the entire hardware domain of the mainframe world has been characterized by an unmatched, and indeed accelerating, evolution.
Mainframes used to be defined by their size, and they can still fill a room, cost millions, and support thousands of users. But now a mainframe can also run on a laptop and support two users. So today's mainframes are best defined by their operating systems: Unix and Linux, and IBM's z/OS, OS/390, MVS, VM, and VSE. Mainframes combine four important features: 1) Reliable single-thread performance, which is essential for reasonable operations against a database. 2) Maximum I/O connectivity, which means mainframes excel at providing for huge disk farms. 3) Maximum I/O bandwidth, so connections between drives and processors have few choke-points. 4) Reliability--mainframes often allow for "graceful degradation" and service while the system is running.
A mainframe is a continually evolving general purpose computing platform incorporating in it architectural definition the essential functionality required by its target applications."
Some additional comments about this definition are in order. One of the most fundamental features of the mainframe world is the rapid and apparently endless evolution of the product line. From 16 general and 4 floating point registers of System/360, to the control register additions in the early 370s, to the access registers of the latter 370s, to the full complement of floating point registers of System/390 and the full 64 bit implementation offered by the z800/900 models; from 6 selector channels to 16 block multiplexing channels to 256 high speed optical channels; from 142 instructions to over 500 instructions; from real addressing to virtual addressing to virtual machines; from the simple 8 bit memory of the 360/30 through generations of development to the multiported, multilevel caching, multiprocessor supporting memory of the z900, the entire hardware domain of the mainframe world has been characterized by an unmatched, and indeed accelerating, evolution.
Mainframes used to be defined by their size, and they can still fill a room, cost millions, and support thousands of users. But now a mainframe can also run on a laptop and support two users. So today's mainframes are best defined by their operating systems: Unix and Linux, and IBM's z/OS, OS/390, MVS, VM, and VSE. Mainframes combine four important features: 1) Reliable single-thread performance, which is essential for reasonable operations against a database. 2) Maximum I/O connectivity, which means mainframes excel at providing for huge disk farms. 3) Maximum I/O bandwidth, so connections between drives and processors have few choke-points. 4) Reliability--mainframes often allow for "graceful degradation" and service while the system is running.
How to Search & Replace Multiple Files in UNIX
Step 1 Open a blank file in any text editor.
Step 2 Place the following script into the the text editor:
#!/bin/bash
#
echo "Type your find string followed by [Enter]:"
read fstring
echo "Type your replace string followed by [Enter]:"
read rstring
for y in `ls *`;
do sed "s/$fstring/$rstring/g" $y > temp; mv temp $y;
done
Step 3Save the script with the name "findrep.sh" in the same directory as the files you want to manipulate.
Step 4Open a Terminal Window. The terminal window will be found in the operating system's main "Application" menu, under either "System Tools" or "Utilities." You will be presented with a command prompt where you will type the following commands.
Step 5Type the command "mv" to move into the directory with the script. For example, the command would be "mv Files/" if the script was held in the "Files" directory in your home directory.
Step 6Type the command "chmod +x findrep.sh" to make the file executable.
Step 7Type the command "./findrep.sh" to execute the script.
Step 2 Place the following script into the the text editor:
#!/bin/bash
#
echo "Type your find string followed by [Enter]:"
read fstring
echo "Type your replace string followed by [Enter]:"
read rstring
for y in `ls *`;
do sed "s/$fstring/$rstring/g" $y > temp; mv temp $y;
done
Step 3Save the script with the name "findrep.sh" in the same directory as the files you want to manipulate.
Step 4Open a Terminal Window. The terminal window will be found in the operating system's main "Application" menu, under either "System Tools" or "Utilities." You will be presented with a command prompt where you will type the following commands.
Step 5Type the command "mv
Step 6Type the command "chmod +x findrep.sh" to make the file executable.
Step 7Type the command "./findrep.sh" to execute the script.
How to Remove Duplicate Lines in Unix
File Can be Sorted Alphabetically
Step 1Make a backup of the file you are working with:
cp document.txt document.txt.bkup
Step 2Issue the command:
sort -u document.txt
This command will sort the file and remove all duplicate lines.
Step 3Remove the blank lines with the command:
uniq document.txt
File Cannot be Sorted Alphabetically
Step 1Make a backup file:
cp document.txt document.txt.bkup
Step 2Issue the following awk command:
awk '!($0 in a) {a[$0];print}' document.txt > unique.txt
Your unique entries will be found in the file named unique.txt
Step 3Rename the text file with the unique lines.
cp unique.txt document.txt
This puts the unique entries back into the original file.
Combine Two Files and Find the Duplicate Lines
Step 1Make a backup file:
cp document.txt document.txt.bkup
Step 2Issue the command:
cat doc1.txt doc2.txt > combine.txt
This command combines doc1.txt and doc2.txt into the file combine.txt
Step 3Remove the duplicate lines.
Use either the sort and uniq commands or the awk command specified above.
Step 1Make a backup of the file you are working with:
cp document.txt document.txt.bkup
Step 2Issue the command:
sort -u document.txt
This command will sort the file and remove all duplicate lines.
Step 3Remove the blank lines with the command:
uniq document.txt
File Cannot be Sorted Alphabetically
Step 1Make a backup file:
cp document.txt document.txt.bkup
Step 2Issue the following awk command:
awk '!($0 in a) {a[$0];print}' document.txt > unique.txt
Your unique entries will be found in the file named unique.txt
Step 3Rename the text file with the unique lines.
cp unique.txt document.txt
This puts the unique entries back into the original file.
Combine Two Files and Find the Duplicate Lines
Step 1Make a backup file:
cp document.txt document.txt.bkup
Step 2Issue the command:
cat doc1.txt doc2.txt > combine.txt
This command combines doc1.txt and doc2.txt into the file combine.txt
Step 3Remove the duplicate lines.
Use either the sort and uniq commands or the awk command specified above.
Awk Tutorial in Unix,Examples of Using AWK
The Unix operating system is one of the most diverse and powerful operating systems ever devised. Created in the late 1960s, Unix provides a stable platform for many business operations globally to this day. Unix administrators use a robust set of commands to tune and support the Unix operating system, and AWK is a part of the language that processes files of text. In essence, AWK allows one to grab certain bits of data from output in the Unix operating system.
Examples of Using AWK
We will continue to look at this command line "# more samplefile | awk '{print $1}' and discuss how AWK can pull data from the "samplefile" file.
If you were to read "samplefile" on its own, the data output might look like this:
# more samplefile
Device File ALPA Tgt Lun Port CU:LDev Type Serial#
=======================================================
/dev/hai/567hyu 00 00 00 CL5A 07:6c OPEN-V 00030052
/dev/hai/c37t8d0 00 08 00 CL6A 07:6c OPEN-V 00030052
But let's say you only want the first field of data from this output. You could use the following AWK command to accomplish this.
# more samplefile | awk '{print $1}' | more
Device
======================================================
/dev/hai/567hyu
/dev/hai/c37t8d0
You could even take it a step further. Let us say that you only want the number that is listed in the output and not the /dev/hai/ part. In that case you would use the operator "awk --F" to act as a field separator. The great thing is that you can decide the field separator. Here is the command you would use.
# more samplefile | awk '{print $1}' | awk --F / '{print $4}' | more
567hyu
c37t8d0
In this case you are using AWK twice. The first time you are grabbing the first field of data, and the second time you are taking that first field, dividing it at the "/", and then pulling out the fourth field in this new group, which leaves you with only the numbers you wanted.
This was just a short example of how AWK comes in handy so that Unix Administrators can quickly filter and grab out only the most important bits of data.
Examples of Using AWK
We will continue to look at this command line "# more samplefile | awk '{print $1}' and discuss how AWK can pull data from the "samplefile" file.
If you were to read "samplefile" on its own, the data output might look like this:
# more samplefile
Device File ALPA Tgt Lun Port CU:LDev Type Serial#
=======================================================
/dev/hai/567hyu 00 00 00 CL5A 07:6c OPEN-V 00030052
/dev/hai/c37t8d0 00 08 00 CL6A 07:6c OPEN-V 00030052
But let's say you only want the first field of data from this output. You could use the following AWK command to accomplish this.
# more samplefile | awk '{print $1}' | more
Device
======================================================
/dev/hai/567hyu
/dev/hai/c37t8d0
You could even take it a step further. Let us say that you only want the number that is listed in the output and not the /dev/hai/ part. In that case you would use the operator "awk --F" to act as a field separator. The great thing is that you can decide the field separator. Here is the command you would use.
# more samplefile | awk '{print $1}' | awk --F / '{print $4}' | more
567hyu
c37t8d0
In this case you are using AWK twice. The first time you are grabbing the first field of data, and the second time you are taking that first field, dividing it at the "/", and then pulling out the fourth field in this new group, which leaves you with only the numbers you wanted.
This was just a short example of how AWK comes in handy so that Unix Administrators can quickly filter and grab out only the most important bits of data.
Basic Framework of JCL
| /name | JOB | parameters... |
| //name | EXEC | parameters... |
| //name | DD | parameters... |
Each of this JCL Statements have a label – a symbolic name assigned to them. Its like naming kids. Well, there could be so many boys in your area, but how do distinguish them? Of course, by their names.
In the same way, a JCL may contain a bunch of DD Statements, one for Input file, one for the output file, one for the error file. How do you tell them apart, by naming them. As a good practice, we always give names to all our JCL Statements. Names kinda help you to refer back to these statements in the future. You want to point out a particular JCL Statement to your friend, just spell out its name.
But, notice carefully, each label(name) is preceded with two slashes //. The two slashes are a JCL Statement’s signature. They indicate that the statement is a JCL Statement(one of JOB, EXEC, DD). Every JCL Statement wear the two slashes //. A naked statement without // won’t be treated as a JCL Statement.
Now, every JOB, EXEC and DD Statement has got these whole lot of parameters. What you’ll be learning throughout these tutorials is mostly the parameters. Parameters add stuff and meaning to the JCL Statement.
Now, let me give you a booster, that’s going to help you organise the way you think about this JCL.
- JCL is made up of mainly JOB, EXEC and DD.
- JOB is easy to learn and use.
- EXEC is easy and fun to use.
- DD Statements take three forms
1. DD Statements to read a file.(easy)
2. DD Statements to write to the logs.(easy)
3. DD Statements to create a new file(hard!); you’d have to learn parameters such as DISP, UNIT, DCB, SPACE and several others to code this.
Have a good look at this chart :
![Image99[1] Image99[1]](http://lh5.ggpht.com/_sQvdFWqMlMg/S1lNA0tMhQI/AAAAAAAACII/2j7bobiqcpE/Image99%5B1%5D_thumb%5B3%5D.png?imgmax=800)
Improve your jQuery - 25 excellent tips
jQuery is awesome. I've been using it for about a year now and although I was impressed to begin with I'm liking it more and more the longer I use it and the more I find out about it's inner workings.
I'm no jQuery expert. I don't claim to be, so if there are mistakes in this article then feel free to correct me or make suggestions for improvements.
I'd call myself an "intermediate" jQuery user and I thought some others out there could benefit from all the little tips, tricks and techniques I've learned over the past year. The article also ended up being a lot longer than I thought it was going to be so I'll start with a table of contents so you can skip to the bits you're interested in.
Table of Contents
* 1. Load the framework from Google Code
* 2. Use a cheat sheet
* 3. Combine all your scripts and minify them
* 4. Use Firebug's excellent console logging facilities
* 5. Keep selection operations to a minimum by caching
* 6. Keep DOM manipulation to a minimum
* 7. Wrap everything in a single element when doing any kind of DOM insertion
* 8. Use IDs instead of classes wherever possible
* 9. Give your selectors a context
* 10. Use chaining properly
* 11. Learn to use animate properly
* 12. Learn about event delegation
* 13. Use classes to store state
* 14. Even better, use jQuery's internal data() method to store state
* 15. Write your own selectors
* 16. Streamline your HTML and modify it once the page has loaded
* 17. Lazy load content for speed and SEO benefits
* 18. Use jQuery's utility functions
* 19. Use noconflict to rename the jquery object when using other frameworks
* 20. How to tell when images have loaded
* 21. Always use the latest version
* 22. How to check if an element exists
* 23. Add a JS class to your HTML attribute
* 24. Return 'false' to prevent default behaviour
* 25. Shorthand for the ready event
I'm no jQuery expert. I don't claim to be, so if there are mistakes in this article then feel free to correct me or make suggestions for improvements.
I'd call myself an "intermediate" jQuery user and I thought some others out there could benefit from all the little tips, tricks and techniques I've learned over the past year. The article also ended up being a lot longer than I thought it was going to be so I'll start with a table of contents so you can skip to the bits you're interested in.
Table of Contents
* 1. Load the framework from Google Code
* 2. Use a cheat sheet
* 3. Combine all your scripts and minify them
* 4. Use Firebug's excellent console logging facilities
* 5. Keep selection operations to a minimum by caching
* 6. Keep DOM manipulation to a minimum
* 7. Wrap everything in a single element when doing any kind of DOM insertion
* 8. Use IDs instead of classes wherever possible
* 9. Give your selectors a context
* 10. Use chaining properly
* 11. Learn to use animate properly
* 12. Learn about event delegation
* 13. Use classes to store state
* 14. Even better, use jQuery's internal data() method to store state
* 15. Write your own selectors
* 16. Streamline your HTML and modify it once the page has loaded
* 17. Lazy load content for speed and SEO benefits
* 18. Use jQuery's utility functions
* 19. Use noconflict to rename the jquery object when using other frameworks
* 20. How to tell when images have loaded
* 21. Always use the latest version
* 22. How to check if an element exists
* 23. Add a JS class to your HTML attribute
* 24. Return 'false' to prevent default behaviour
* 25. Shorthand for the ready event
ASP.NET AJAX mistakes
It’s important to remember that a partial postback is just that: A postback.
The UpdatePanel’s way of abstracting AJAX functionality behind standard WebForm methodology provides us with flexibility and familiarity. However, this also means that using an UpdatePanel requires careful attention to the ASP.NET Page Life Cycle.
In this post, I’d like to point out a few of the problems I’ve seen developers running into and what you can keep in mind to avoid them:
Page.IsPostBack is true during partial postbacks, making it easy to avoid this pitfall. However, it’s a problem that surfaces at least daily on the ASP.NET forums, so it bears mentioning.
Additionally, ScriptManager.IsInAsyncPostBack is true during partial postbacks only. This property can be used to further distinguish what type of request is being processed.
Even if you’re using UpdatePanels with conditional UpdateModes and some of those UpdatePanels aren’t being visibly updated in a given partial postback, all of them will be recreated on the server and execute any life cycle event handlers you’ve wired up for them.
Typically, this means that should wrap your code in an !IsPostBack or !IsInAsyncPostBack conditional if you don’t want it to execute on every request. However, one slightly more tricky situation is when you want to execute code only if a particular UpdatePanel is targeted for a refresh. To accomplish that, you can check the __EVENTTARGET:
Basically, he had an UpdatePanel and Button interacting with each other to create a simple poll. The UpdatePanel’s Load event rendered poll results from a database table, while Button_Click let users submit their poll votes to the database.
Can you see the problem?
If you read the subheading above, it’s probably obvious. Button_Click was running after UpdatePanel_Load, giving his users the impression that their votes were not being counted since the display didn’t change when they voted.
The fix? Instead of rendering the poll in UpdatePanel_Load, he needed to render it in the PreRender event instead, because UpdatePanel_PreRender fires after Button_Click.
It sounds simple when spelled out, but it’s a mistake we’ve probably all made at one time or another. The extra layer of complexity that AJAX brings to the table only makes it easier to accidentally forget about subtle page life cycle issues.
The UpdatePanel’s way of abstracting AJAX functionality behind standard WebForm methodology provides us with flexibility and familiarity. However, this also means that using an UpdatePanel requires careful attention to the ASP.NET Page Life Cycle.
In this post, I’d like to point out a few of the problems I’ve seen developers running into and what you can keep in mind to avoid them:
- Page events still fire during partial postbacks.
- UpdatePanel events fire, even when not updating.
- Control event handlers fire after Load events.
Page events still fire during partial postbacks
One of the most common things that new ASP.NET AJAX developers overlook is that all of the Page’s life cycle events (Page_Load, Page_PreRender, etc) do execute during every partial postback. During a partial postback, the Page’s control tree is fully reinstantiated and every single control runs through its life cycle events. If that’s not taken into account, it’s very easy to run into mysterious difficulties.Page.IsPostBack is true during partial postbacks, making it easy to avoid this pitfall. However, it’s a problem that surfaces at least daily on the ASP.NET forums, so it bears mentioning.
Additionally, ScriptManager.IsInAsyncPostBack is true during partial postbacks only. This property can be used to further distinguish what type of request is being processed.
UpdatePanel events fire on each and every request
Using the UpdatePanel’s life cycle events (Init, Load, PreRender, and Unload) can be a great way to partition your code and enables you to use __doPostBack() to trigger the UpdatePanel from JavaScript. However, it is crucial to understand that these events will execute on every page load, postback, and partial postback.Even if you’re using UpdatePanels with conditional UpdateModes and some of those UpdatePanels aren’t being visibly updated in a given partial postback, all of them will be recreated on the server and execute any life cycle event handlers you’ve wired up for them.
Typically, this means that should wrap your code in an !IsPostBack or !IsInAsyncPostBack conditional if you don’t want it to execute on every request. However, one slightly more tricky situation is when you want to execute code only if a particular UpdatePanel is targeted for a refresh. To accomplish that, you can check the __EVENTTARGET:
protected void UpdatePanel1_PreRender(object sender, EventArgs e) { // This code will only be executed if the partial postback // was raised by a __doPostBack('UpdatePanel1', '') if (Request["__EVENTTARGET"] == UpdatePanel1.ClientID) { // Insert magic here. } }
Control events are raised after Load events
One of my readers recently ran into what is probably the second most common page life cycle problem I’ve seen.Basically, he had an UpdatePanel and Button interacting with each other to create a simple poll. The UpdatePanel’s Load event rendered poll results from a database table, while Button_Click let users submit their poll votes to the database.
Can you see the problem?
If you read the subheading above, it’s probably obvious. Button_Click was running after UpdatePanel_Load, giving his users the impression that their votes were not being counted since the display didn’t change when they voted.
The fix? Instead of rendering the poll in UpdatePanel_Load, he needed to render it in the PreRender event instead, because UpdatePanel_PreRender fires after Button_Click.
It sounds simple when spelled out, but it’s a mistake we’ve probably all made at one time or another. The extra layer of complexity that AJAX brings to the table only makes it easier to accidentally forget about subtle page life cycle issues.
Oracle vs. Sybase: 10 reasons to use Sybase on Linux
Sybase products are generally perceived within the database administrator (DBA) community as very reliable and easy to maintain, particularly compared to Oracle. Any move from Sybase to another DBMS (database management system) has got to be justified in terms of the current level of dissatisfaction with Sybase and the level of desire to use the other. I cannot recall anywhere where this is valid.
By Mich Talebzedah
SearchOracle.com
- The latest Sybase flagship product, ASE 15, has filled much of the perceived functionality gap between ASE and other databases.
- Linux is an ideal and cost-effective platform for development teams and many companies. With the availability of heterogeneous dump and load of Sybase databases across different operating systems, Sybase -- by virtue of its modularity and ease of use -- is an ideal DBMS for Linux. This needs to be contrasted with Oracle which is, pound for pound, a far heavier beast and resource-hungry.
- Sybase has a well-established and skilled workforce, offering infrastructure and development teams who are fully familiar with database architectures and Sybase products.
- Applications developed using Sybase have been running for a while and providing adequate service.
By Mich Talebzedah
SearchOracle.com
How to pass value from main report to sub report?
Here's a detailed example:
1. In main report create a formula, name it, edit it with the formula editor as follows:
1. In main report create a formula, name it, edit it with the formula editor as follows:
shared numbervar NAME := {table1.field1} + {table1.field2}Save formula.note that you should replace the name and type of variable and a formula with ones of your own2. Now create a formula in your subreport, name it, edit it with the formula editor as follows:
Shared numbervar NAME;
NAMESave formula.3. Use formula created in step 2 in your report.
This way you will have a {table1.field1} + {table1.field2} result from main report transferred to your subreport.
10 cool features to look forward to in Microsoft Office 2010
Are you excited about the upcoming Office 2010? Some pundits are saying the Office 2010 is to Office 2007 as Win 7 is to Vista—-in the sense that both newer versions are excellent refinements to what were perceived to be RADICALLY new, original products. I know the Ribbon Bar alone caused huge disconsternation at my place of business. Microsoft has listened, and here are 10 cool things that 2010 does as an improvement to 2007. The ability to customize the Ribbon Bar to my most used commands alone is a huge improvement!
Read the Tech Republic Article here: 10 cool features to look forward to in Office 2010 | 10 Things | TechRepublic.com
Read the Tech Republic Article here: 10 cool features to look forward to in Office 2010 | 10 Things | TechRepublic.com
IBM- DB2 for Linux, UNIX and Windows Features and Benefits
Did you know that DB2 can also lower your overall cost of managing data? Here are just some of the many ways
Autonomics
Reliability
Security
Performance
Comprehensive Tools
Virtualiztaion
Autonomics
Reliability
Security
Performance
Comprehensive Tools
Virtualiztaion
My SQL Server Programming-Kill Spid?
Here's a little snippet from an SP i wrote a couple of years ago when i wanted to drop a db. Given the id of the database (@DR_ID), killed my processes just fine...
Get the dbid using the db_id() function.
-- Get a cursor with the processes that have to die in order to be able to drop db
DECLARE curProcesses CURSOR
LOCAL
FAST_FORWARD
READ_ONLY
FOR
SELECT spid
FROM
Master..sysprocesses
WHERE
dbid = @nDR_ID
OPEN curProcesses
FETCH NEXT FROM curProcesses INTO --Gets the first process
@nKillProcess
SET @nFetchStatus = @@FETCH_STATUS
--Kill the processes
WHILE @nFetchStatus = 0
BEGIN
SET @sTemp ='KILL ' + CAST(@nKillProcess as varchar(5))
EXEC(@sTemp)
FETCH NEXT FROM curProcesses INTO --Gets the next process
@nKillProcess
SET @nFetchStatus = @@FETCH_STATUS
END
CLOSE curProcesses
DEALLOCATE curProcesses
Get the dbid using the db_id() function.
-- Get a cursor with the processes that have to die in order to be able to drop db
DECLARE curProcesses CURSOR
LOCAL
FAST_FORWARD
READ_ONLY
FOR
SELECT spid
FROM
Master..sysprocesses
WHERE
dbid = @nDR_ID
OPEN curProcesses
FETCH NEXT FROM curProcesses INTO --Gets the first process
@nKillProcess
SET @nFetchStatus = @@FETCH_STATUS
--Kill the processes
WHILE @nFetchStatus = 0
BEGIN
SET @sTemp ='KILL ' + CAST(@nKillProcess as varchar(5))
EXEC(@sTemp)
FETCH NEXT FROM curProcesses INTO --Gets the next process
@nKillProcess
SET @nFetchStatus = @@FETCH_STATUS
END
CLOSE curProcesses
DEALLOCATE curProcesses
Microsoft Surface Diagram: How it all works
The Microsoft Surface is a revolutionary piece of equipment that has basically brought the major film Minority Report to life, we never imagined something so futuristic would be here with is in 2007. This is heaven to us and we guess it is to you as well, the way this new Touch Surface high tech table works is mind blowing but below we have 4 simple steps of how the Microsoft Surface works.
Microsoft Surface Diagram

1) Screen –
• There is a diffuser which turns the Surface’s acrylic tabletop into a large horizontal “multitouch” screen, which is capable of processing multiple inputs from multiple users. The Surface is so far advanced than we could imagine that it can recognize objects by their shapes or by reading coded “domino” tags when placed on the table.
2) Infrared –
• Surface’s “machine vision” operates in the near-infrared spectrum, using an 850-nanometer-wavelength LED light source aimed at the screen. When objects touch the tabletop, the light reflects back and is picked up by multiple infrared cameras with a net resolution of 1280 x 960.
3) CPU –
• Surface uses many of the same components found in everyday desktop computers — a Core 2 Duo processor, 2GB of RAM and a 256MB graphics card. Wireless communication with devices on the surface is handled using WiFi and Bluetooth antennas (future versions may incorporate RFID or Near Field Communications). The underlying operating system is a modified version of Microsoft Vista.
4) Projector -
• Microsoft’s Surface uses the same DLP light engine found in many rear-projection HDTV’s. The footprint of the visible light screen, at 1024 x 768 pixels, is actually smaller than the invisible overlapping infrared projection to allow for better recognition at the edges of the screen.
Microsoft Surface Diagram

1) Screen –
• There is a diffuser which turns the Surface’s acrylic tabletop into a large horizontal “multitouch” screen, which is capable of processing multiple inputs from multiple users. The Surface is so far advanced than we could imagine that it can recognize objects by their shapes or by reading coded “domino” tags when placed on the table.
2) Infrared –
• Surface’s “machine vision” operates in the near-infrared spectrum, using an 850-nanometer-wavelength LED light source aimed at the screen. When objects touch the tabletop, the light reflects back and is picked up by multiple infrared cameras with a net resolution of 1280 x 960.
3) CPU –
• Surface uses many of the same components found in everyday desktop computers — a Core 2 Duo processor, 2GB of RAM and a 256MB graphics card. Wireless communication with devices on the surface is handled using WiFi and Bluetooth antennas (future versions may incorporate RFID or Near Field Communications). The underlying operating system is a modified version of Microsoft Vista.
4) Projector -
• Microsoft’s Surface uses the same DLP light engine found in many rear-projection HDTV’s. The footprint of the visible light screen, at 1024 x 768 pixels, is actually smaller than the invisible overlapping infrared projection to allow for better recognition at the edges of the screen.
How to Kill All Processes That Have Open Connection in a SQL
The below code block can be used to kill all the processes which are connected to the database named @dbname except the process that the code block is running in the scope of. You can also set the database name by the DB_NAME() property.
DECLARE @dbname nvarchar(50)
DECLARE @SPId int
SET @dbname = N'Works'
--SET @dbname = DB_NAME()
DECLARE my_cursor CURSOR FAST_FORWARD FOR
SELECT SPId FROM MASTER..SysProcesses
WHERE DBId = DB_ID(@DatabaseName) AND SPId <> @@SPId
OPEN my_cursor
FETCH NEXT FROM my_cursor INTO @SPId
WHILE @@FETCH_STATUS = 0
BEGIN
KILL @SPId
FETCH NEXT FROM my_cursor INTO @SPId
END
CLOSE my_cursor
DEALLOCATE my_cursor MySQL 5.0 vs. Microsoft SQL Server 2005
Database engines are a crucial fixture for businesses today. There is no shortage of both commercial and open source database engines to choose from. Microsoft SQL Server 2005 is Microsoft’s next-generation data management solution that claims to deliver secure and scalable applications while making them easy to deploy and manage. MySQL has long been the DBMS of choice in the open source community. The recent release of MySQL 5.0 has seen major changes in both features and performance to bring the database system into enterprise-level standards.
This paper aims to give the low-down on features most desirable to database developers and compare both database management systems in light of these features.
View Complete article here
This paper aims to give the low-down on features most desirable to database developers and compare both database management systems in light of these features.
View Complete article here
7 Best Skills that Every Programmer and Developer should Know
1. All development aspects
The “code” (implementation) is not a stand-alone artifact. It is related with the other development aspects. Example: the code design shall have a good enough modeling of the business domain aspects.
That means the developer (programmer) shall understand and know all these aspects. A good developer SHALL ACT LIKE A TEAM or shall know all the teams’ acts.
For that the “great developer” shall understand and have experience in all others development roles (PM, architect, designer, analyst, tester etc) and a good understanding of software methodologies.
2. Quality evolution versus successive projects
There is no absolute quality. There is only quality in context of one or more projects. A project can have constrains related to SCOPE, TIME and QUALITY. The next project on the same product could have other constrains related to these aspects. The development team shall consider also short, medium, and long term constraints. That mean if the first project was with great time constraint and less quality restrictions, the development team shall be able to restore the quality on the next projects. That is possible only if some development rules are respected.
A great developer shall be able to manage that.
3. Quality management
Quality can be achieved only by quality management: plan quality, assure quality, control quality and continuously improve the process.
4. Quality basic instruments in software: architecture & code quality
- shall be a good architect
- shall be good designer
- shall know to adapt: when “simple design” is required and when need a more elaborated design
5. One man team or team leading
A perfect developer shall be able to replace a team or any team missing parts.
- Good multi-disciplinary knowledge and skills in software domain
- Project & Team leadership’s skills, coaching, training
6. Agility
One team man shall be super-agile. For that, mandatory requirements for agile development shall be fulfilled:
- multi-disciplinarily
- senior skills in development
- senior skills in refactoring
- senior skills in communication
- great problem solving skills
- capability to work in a team or independently
7. Technologies
- shall have a good experience with different technologies
- shall be able to adapt to the new technologies
The “code” (implementation) is not a stand-alone artifact. It is related with the other development aspects. Example: the code design shall have a good enough modeling of the business domain aspects.
That means the developer (programmer) shall understand and know all these aspects. A good developer SHALL ACT LIKE A TEAM or shall know all the teams’ acts.
For that the “great developer” shall understand and have experience in all others development roles (PM, architect, designer, analyst, tester etc) and a good understanding of software methodologies.
2. Quality evolution versus successive projects
There is no absolute quality. There is only quality in context of one or more projects. A project can have constrains related to SCOPE, TIME and QUALITY. The next project on the same product could have other constrains related to these aspects. The development team shall consider also short, medium, and long term constraints. That mean if the first project was with great time constraint and less quality restrictions, the development team shall be able to restore the quality on the next projects. That is possible only if some development rules are respected.
A great developer shall be able to manage that.
3. Quality management
Quality can be achieved only by quality management: plan quality, assure quality, control quality and continuously improve the process.
4. Quality basic instruments in software: architecture & code quality
- shall be a good architect
- shall be good designer
- shall know to adapt: when “simple design” is required and when need a more elaborated design
5. One man team or team leading
A perfect developer shall be able to replace a team or any team missing parts.
- Good multi-disciplinary knowledge and skills in software domain
- Project & Team leadership’s skills, coaching, training
6. Agility
One team man shall be super-agile. For that, mandatory requirements for agile development shall be fulfilled:
- multi-disciplinarily
- senior skills in development
- senior skills in refactoring
- senior skills in communication
- great problem solving skills
- capability to work in a team or independently
7. Technologies
- shall have a good experience with different technologies
- shall be able to adapt to the new technologies
NetBeans IDE 6.9 Beta released!!!!
NetBeans IDE 6.9 Beta Release Information
The NetBeans IDE is an award-winning integrated development environment available for Windows, Mac, Linux, and Solaris. The NetBeans project consists of an open-source IDE and an application platform that enable developers to rapidly create web, enterprise, desktop, and mobile applications using the Java platform, as well as JavaFX, PHP, JavaScript and Ajax, Ruby and Ruby on Rails, Groovy and Grails, and C/C++.
Review:
NetBeans 6.9 Beta introduces the JavaFX Composer, a visual layout tool for visually building JavaFX GUI applications, similar to the Swing GUI builder for Java SE applications. Additional highlights include OSGi interoperability for NetBeans Platform applications and support for developing OSGi bundles with Maven; support for JavaFX SDK 1.3, PHP Zend framework, and Ruby on Rails 3.0; as well as improvements to the Java Editor, Java Debugger, issue tracking, and more.
Visit http://download.netbeans.org/netbeans/6.9/beta/ for more details
Create Installer for Java Application
Today, I came across a good article mentioning how to convert your java application into a installer and distribute it. There is an option to add JRE, obfuscate the code and make .exe of java programme in that.
Read it here
Read it here
5 Best Habits of Software Developers
This article illustrates five habits of software development teams that make them more effective and therefore more profitable. It first will describe the demands the business team puts on its software development team and the software they create.
Next it will explain the important differences between state-changing logic and behavior logic.
Finally, it will illustrate the five habits using a customer account scenario as a case study.
There are many; and many of these are specific to types of work. I shall try and list some of the most important. Bear in mind that there's a lot hiding under each of the topics I list.
1. Treat every defect as an opportunity to learn; how did the defect get there? What can be done to prevent that type of defect happeining again?
2. Simple Design. Think about how much you can take away and still meet the requirements, rather than how fancy a solution you can build to the requirements. Keep a look out for code duplication - where the same decision is made in more than one part of the code.
3. Communicate. You can learn something from everybody. Talk to the people who are providing the requirements, who will use the system, who will test what you design, who are designing other parts of the system, who are looking at the overall architecture - if there are such people for your system.
4. Learn. All the time. Everything. I guess this isn't essential, but all the top developers I've ever met seem to do this, so I think I see a pattern...
5. Be able to work in other peope's roles. You don't need to be good at everything, but know enough about the basics of testing, requirements gathering, architecture, live support, project management etc. that you could cover those roles for a short period, with help.
6. Teach. Not all the time, but trying to explain concepts to other people is a great way of getting them straight in your own mind.
Next it will explain the important differences between state-changing logic and behavior logic.
Finally, it will illustrate the five habits using a customer account scenario as a case study.
There are many; and many of these are specific to types of work. I shall try and list some of the most important. Bear in mind that there's a lot hiding under each of the topics I list.
1. Treat every defect as an opportunity to learn; how did the defect get there? What can be done to prevent that type of defect happeining again?
2. Simple Design. Think about how much you can take away and still meet the requirements, rather than how fancy a solution you can build to the requirements. Keep a look out for code duplication - where the same decision is made in more than one part of the code.
3. Communicate. You can learn something from everybody. Talk to the people who are providing the requirements, who will use the system, who will test what you design, who are designing other parts of the system, who are looking at the overall architecture - if there are such people for your system.
4. Learn. All the time. Everything. I guess this isn't essential, but all the top developers I've ever met seem to do this, so I think I see a pattern...
5. Be able to work in other peope's roles. You don't need to be good at everything, but know enough about the basics of testing, requirements gathering, architecture, live support, project management etc. that you could cover those roles for a short period, with help.
6. Teach. Not all the time, but trying to explain concepts to other people is a great way of getting them straight in your own mind.
Microsoft Visual Studio 2010 Express Features and latest Updates
The Visual Studio 2010 Express is a set of free tools which offers you an exciting experience with the new integrated development environment, a new editor built in Windows Presentation Foundation (WPF) and support for the new .NET Framework 4
Here are some key features of Visual Studio Express Edition:
- Visual Studio 2010 Express supports the new .NET Framework 4.
- Visual Studio 2010 Express products have a new integrated development environment (IDE) including a new Windows Presentation Framework code editor.
- In this new release, Visual Studio 2010 Express gains multi-monitor support as well as part of the new IDE.
- Unique to Visual Studio 2010 Express is a new streamlined user experience that focuses on the most common commands by hiding some of the more advanced menus and toolbars. These are easily accessible by users via the Tools / Settings menu.a
Here are some key features of Visual Studio Express Edition:
- Visual Studio 2010 Express supports the new .NET Framework 4.
- Visual Studio 2010 Express products have a new integrated development environment (IDE) including a new Windows Presentation Framework code editor.
- In this new release, Visual Studio 2010 Express gains multi-monitor support as well as part of the new IDE.
- Unique to Visual Studio 2010 Express is a new streamlined user experience that focuses on the most common commands by hiding some of the more advanced menus and toolbars. These are easily accessible by users via the Tools / Settings menu.a
Microsoft Visual Studio 2010 Express gets more cloud-computing friendly
The just launched Visual Studio 2010 is packed with plenty of new functionalities and features, including better integration with the Windows Azure cloud computing platform, which should put local software developers on Cloud 9.
With Windows Azure Tools, developers can quickly write, test, debug and deploy cloud applications from within the familiar Visual Studio environment, said Microsoft Malaysia at the launch.
To address the growing complexity of software development, Visual Studio 2010 also ships with the powerful IntelliTrace tool.
Described as a “time machine for developers and testers,” this tool makes non-reproducible bugs a thing of the past.
It enables developers to record an application’s execution history, which guarantees reproduction of any bugs to allow a tester to easily find it again, and to iron out the glitch once and for all.
Also new is multi-monitor support to enable a developer to “tear off” any window, such as a code or trace information application, and dock it in a separate display for much easier viewing.
During the launch, Microsoft also unveiled an updated .NET Framework 4, which now has additional support for various industry standards — and thanks to the inclusion of Dynamic Language Runtime, more language choices for users.
The revamped product now also supports high-performance middle-tier applications, such as parallel programming, workflow and service-oriented applications.
With Windows Azure Tools, developers can quickly write, test, debug and deploy cloud applications from within the familiar Visual Studio environment, said Microsoft Malaysia at the launch.
To address the growing complexity of software development, Visual Studio 2010 also ships with the powerful IntelliTrace tool.
Described as a “time machine for developers and testers,” this tool makes non-reproducible bugs a thing of the past.
It enables developers to record an application’s execution history, which guarantees reproduction of any bugs to allow a tester to easily find it again, and to iron out the glitch once and for all.
Also new is multi-monitor support to enable a developer to “tear off” any window, such as a code or trace information application, and dock it in a separate display for much easier viewing.
During the launch, Microsoft also unveiled an updated .NET Framework 4, which now has additional support for various industry standards — and thanks to the inclusion of Dynamic Language Runtime, more language choices for users.
The revamped product now also supports high-performance middle-tier applications, such as parallel programming, workflow and service-oriented applications.
5 PHP Mistakes
1. Single quotes, double quotes
It’s easy to just use double quotes when concatenating strings because it parses everything neatly without having to deal with escaping characters and using dot values. However, using single quotes has considerable performance gains, as it requires less processing.Consider this string:
# $howdy = 'everyone'; # $foo = 'hello $howdy'; # $bar = "hello $howdy";$foo outputs to “hello $howdy” and $bar gives us “hello everyone”. That’s one less step that PHP has to process. It’s a small change that can make significant gains in the performance of the code.
2. Semicolon after a While
It’s funny how one little character can create havoc in a program, without even being reported to the PHP error logs! Such as it is with semicolons and While statements.Codeutopia has an excellent example of this little error, showing that these nasty errors don’t even get reported (even to E_ALL!), as it quietly falls into a silent loop.
$i = 0;
while($i < 20); {
//some code here
$i++;
}
Omit the ; after the while statement, and your code is in the clear.3. NOT Using database caching
If you're using a database in your PHP application, it is strongly advised that you at least use some sort of database caching. Memcached has emerged as the most poplar caching system, with mammoth sites like Facebook endorsing the software.Memcached is free and can provide very significant gains to your software. If your PHP is going into production, it's strongly advised to use the caching system.
4. Missing Semicolon After a Break or a Continue
Like #2, a misused semicolon can create serious problems while silently slipping off into the shadows, making it quite difficult to track the error down.If you're using a semicolon after a "break" or "continue" in your code, it will convince the code to output a "0" and exit. This could cause some serious head scratching. You can avoid this by using braces with PHP control structures (via CodeUtopia).
5. Not Using E_ALL Reporting
Error reporting is a very handy feature in PHP, and if you're not already using it, you should really turn it on. Error reporting takes much of the guesswork out of debugging code, and speeds up your overall development time.While many PHP programmers may use error reporting, many aren't utilizing the full extent of error reporting. E_ALL is a very strict type of error reporting, and using it ensures that even the smallest error is reported. (That's a good thing if you're wanting to write great code.)
Subscribe to:
Comments (Atom)
